My earlier post on the Heatmiser PRT-TS wi-fi thermostat proved very popular and is the most commented article on this blog. When commenter Rich mentioned the heatmiser-wifi project, a set of Perl scripts that can be installed on a PC or Raspberry Pi to provide a full-featured web interface for the Heatmiser, I just had to give it a go.
Although the project site mentions that it has been tested on Raspberry Pi, I just couldn’t get past one of the steps. A little bit of Googling revealed a possible solution, and it worked. Be warned, the process takes a little while but in my opinion the results are definitely worth it.
Installation of Subversion and the heatmiser-wifi software
To get hold of the software, you have to check it out using the Subversion (SVN) source control system. So the first step is to install SVN:
sudo apt-get install subversion
You can then run the following command to download the heatmiser-wifi software:
svn checkout http://heatmiser-wifi.googlecode.com/svn/trunk/ ~/heatmiser-wifi-read-only
This will create a folder called heatmiser-wifi-read-only in your home directory. If you want to specify a different path, edit the command as appropriate.
Install Perl and essential packages
Check that Perl version 5 is installed by running:
perl -v
This should return some output starting with the following (or similar):
This is perl, v5.10.1 (*) built for arm-linux-gnueabi-thread-multi
If not, install Perl using:
sudo apt-get update
sudo apt-get install perl5
Now you need to install the required packages:
curl -L http://cpanmin.us | perl - --sudo App::cpanminus
sudo cpanm CGI Cwd DBI File::HomeDir Getopt::Std IO::Socket JSON LWP::UserAgent Proc::Daemon Proc::PID::File Time::HiRes
sudo apt-get install libxml-simple-perl
sudo cpanm XML::Simple
This takes a long time, so you may want to have a cup of tea, run a bath or go for a walk!
(Note that the original instructions had the CPAN modules listed on one line, omitting the apt-get before XML::Simple, but this didn’t work for me, hence the change. Also I had trouble getting the standard cpan command to work on the Pi due to its limited hardware, hence using cpanminus instead.)
Test the installation
Run the following command, adjusting the path if necessary, replacing 192.168.0.100 with the actual IP address of your Heatmiser and 1234 with the PIN number:
~/heatmiser-wifi-read-only/bin/heatmiser.pl -h 192.168.0.100 -p 1234
You should get some output like this:
Heatmiser PRT version 1.2
Thermostat is ON (heating mode)
Time 2012-07-07 21:45:59
Temperature 23.5 deg C (internal)
Target 17 deg C
Heating is OFF
Feature 01: Temperature format C
Feature 02: Switching differential 1 deg C
Feature 03: Frost protect 1
Feature 04: Frost temperature 15 deg C
Feature 05: Output delay 0 minutes
Feature 06: Comms # n/a
Feature 07: Temperature limit 0 deg C
Feature 08: Sensor selection internal
Feature 09: Floor limit n/a
Feature 10: Optimum start disabled hours
Feature 11: Rate of change 20 minutes / deg C
Feature 12: Program mode 5/2 day
Weekday 1: 07:00 20 deg C
2: 07:30 17 deg C
3: 17:00 20 deg C
4: 21:30 17 deg C
Weekend 1: 09:30 20 deg C
2: 21:30 17 deg C
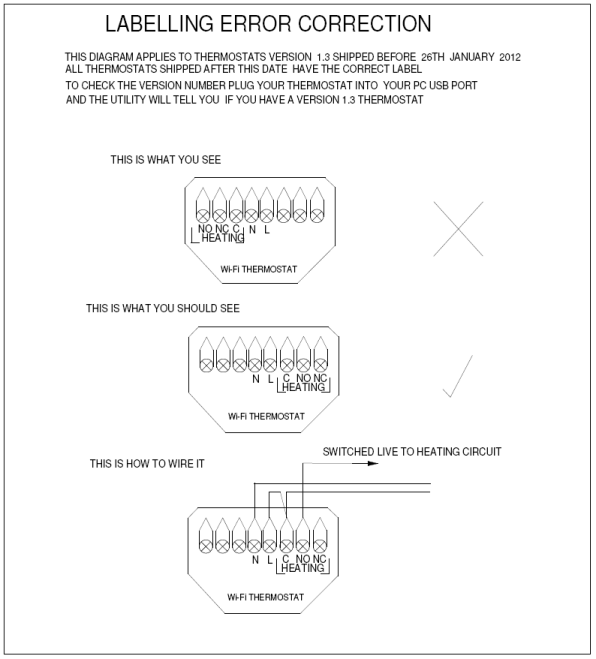
For the rest of the steps to work, you need to store the IP address and PIN number in a config file. To do this:
sudo nano /etc/heatmiser.conf
Type the following two lines, substituting 192.168.0.100 with your thermostat’s actual IP address, and 1234 with its PIN:
HOST 192.168.0.100
PIN 1234
Press Ctrl+X and type Y to save the file.
You should now be able to run the following command (same as before but without the IP and password, which will now be read from the conf file).
~/heatmiser-wifi-read-only/bin/heatmiser.pl
Set up the web interface
Happily the project’s web interface instructions seem to work fine on the Pi without any changes.
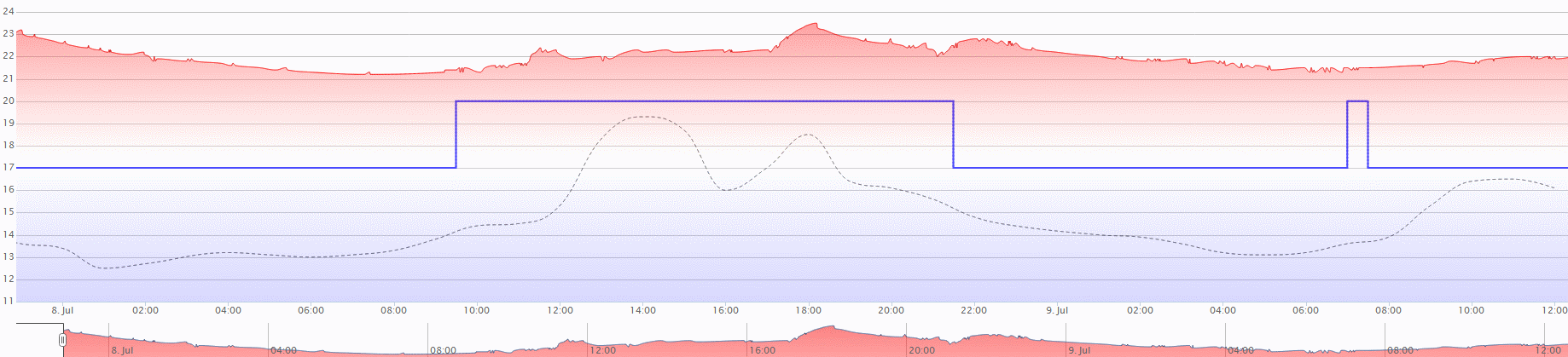
I have also set up logging and charting of external temperature (via the Met Office API). Frustratingly, my Met Office API key didn’t work straight away – it kept returning Invalid key please register at http://www.metoffice.gov.uk/public/ddc via both the heatmiser_weather.pl script and the “preview data” feature on the Met Office site itself. Also note that it will take up to five minutes for the weather table to start populating, unless you’ve increased the rate in the heatmiser.conf file.