Blocking “unsafe” ports is something that Google Chrome has done for a while now, but I’ve only just discovered this feature, trying to connect to an internal host via HTTP on a non-standard port:
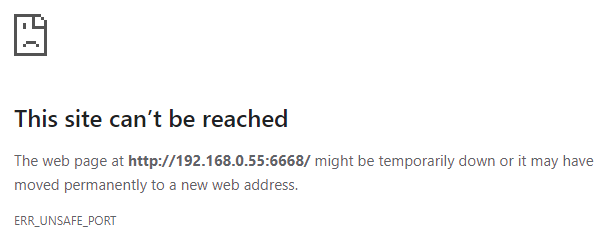
The error message is slightly misleading as the endpoint isn’t down, it’s just being blocked by Chrome – ERR_UNSAFE_PORT is the crucial clue.
This seemed odd to me, but there’s a great explanation here. In a nutshell, it’s an attempt to prevent Chrome being used as a way to attack potentially vulnerable services. Because many implementations of simple plain-text protocols such as SMTP, FTP and Telnet are very tolerant of errors (i.e. simply ignoring commands that don’t make sense), it may be possible for a malicious or compromised website to trick a user’s browser into sending a specially-crafted HTTP request that contains valid commands in the target protocol.
There is an unofficial list of restricted ports here – in my case, the port’s being blocked as it is one of the ports commonly used for IRC (Internet Relay Chat). On desktop Chrome, there is a workaround that allows you to disable this behaviour on a per-port basis, but as far as I can see, there’s no way to do this on the Android version of Chrome. The only real solution is for developers to avoid using these specific non-standard ports for HTTP (there are plenty of other ports to choose from!)
It’s quite an interesting idea, and while in an ideal world there wouldn’t be any services vulnerable to this sort of attack, we all know the reality is quite different. On balance, I think I’m in favour of Google (and Mozilla, who include similar functionality in Firefox) including this simple protection to help make the Web a safer place.
At the time of writing, Internet Explorer on Windows 10 doesn’t seem to block unsafe ports, but the latest version of Edge (which is based on Chromium) gives the same ERR_UNSAFE_PORT error as Chrome.
